Abstract of this communication paper-presentations : (Security in Wi-Fi)
Wireless networks are very common, both for organizations and individuals. Many laptop computers have wireless cards pre-installed. The ability to enter a network while mobile has great benefits. However, wireless networking has many security issues. Hackers have found wireless networks relatively easy to break into, and even use wireless technology to crack into wired networks. As a result, it's very important that enterprises define effective wireless security policies that guard against unauthorized access to important resources. The risks to users of wireless technology have increased as the service has become more popular. There were relatively few dangers when wireless technology was first introduced. However, there are a great number of security risks associated with the current wireless protocols and encryption methods, and in the carelessness and ignorance that exists at the user and corporate IT level. Cracking methods have become much more sophisticated and innovative with wireless.
Types of unauthorized access
Accidental association
Unauthorized access to company wireless and wired networks can come from a number of different methods and intents. One of these methods is referred to as “accidental association”. When a user turns on a computer and it latches on to a wireless access point from a neighboring company’s overlapping network, the user may not even know that this has occurred. However, it is a security breach in that proprietary company information is exposed and now there could exist a link from one company to the other. This is especially true if the laptop is also hooked to a wired network.
Malicious association
“Malicious associations” are when wireless devices can be actively made by crackers to connect to a company network through their cracking laptop instead of a company access point (AP). These types of laptops are known as “soft APs” and are created when a cracker runs some software that makes his/her wireless network card look like a legitimate access point. Once the cracker has gained access, he/she can steal passwords, launch attacks on the wired network, or plant Trojans. Since wireless networks operate at the Layer 2 level, Layer 3 protections such as network authentication and virtual private networks (VPNs) offer no barrier. Wireless 802.1x authentications do help with protection but are still vulnerable to cracking. The idea behind this type of attack may not be to break into a VPN or other security measures. Most likely the cracker is just trying to take over the client at the Layer 2 level.
Ad-hoc networks
Ad-hoc networks can pose a security threat. Ad-hoc networks are defined as peer-to-peer networks between wireless computers that do not have an access point in between them. While these types of networks usually have little protection, encryption methods can be used to provide security.
Non-traditional networks
Non-traditional networks such as personal network Bluetooth devices are not safe from cracking and should be regarded as a security risk. Even barcode readers, handheld PDAs, and wireless printers and copiers should be secured. These non-traditional networks can be easily overlooked by IT personnel who have narrowly focused on laptops and access points.
Identity theft (MAC spoofing)
Identity theft (or MAC spoofing) occurs when a cracker is able to listen in on network traffic and identify the MAC address of a computer with network privileges. Most wireless systems allow some kind of MAC filtering to only allow authorized computers with specific MAC IDs to gain access and utilize the network. However, a number of programs exist that have network “sniffing” capabilities. Combine these programs with other software that allow a computer to pretend it has any MAC address that the cracker desires, and the cracker can easily get around that hurdle.
Man-in-the-middle attacks
A man-in-the-middle attacker entices computers to log into a computer which is set up as a soft AP (Access Point). Once this is done, the hacker connects to a real access point through another wireless card offering a steady flow of traffic through the transparent hacking computer to the real network. The hacker can then sniff the traffic. One type of man-in-the-middle attack relies on security faults in challenge and handshake protocols to execute a “de-authentication attack”. This attack forces AP-connected computers to drop their connections and reconnect with the cracker’s soft AP. Man-in-the-middle attacks are enhanced by software such as LANjack and AirJack, which automate multiple steps of the process. What once required some skill can now be done by script kiddies.
Denial of service
A Denial-of-Service attack (DoS) occurs when an attacker continually bombards a targeted AP (Access Point) or network with bogus requests, premature successful connection messages, failure messages, and/or other commands. These cause legitimate users to not be able to get on the network and may even cause the network to crash. These attacks rely on the abuse of protocols such as the Extensible Authentication Protocol (EAP).
Network injection
In a network injection attack, a cracker can make use of access points that are exposed to non-filtered network traffic, specifically broadcasting network traffic such as “Spanning Tree” (802.1D), OSPF, RIP, and HSRP. The cracker injects bogus networking re-configuration commands that affect routers, switches, and intelligent hubs. A whole network can be brought down in this manner and require rebooting or even reprogramming of all intelligent networking devices.
Caffe Latte attack
The Caffe Latte attack is another way to defeat WEP. It is not necessary for the attacker to be in the area of the network using this exploit. By using a process that targets the Windows wireless stack, it is possible to obtain the WEP key from a remote client. By sending a flood of encrypted ARP requests, the assailant takes advantage of the shared key authentication and the message modification flaws in 802.11 WEP. The attacker uses the ARP responses to obtain the WEP key in less than 6 minutes.
Counteracting security risks
There are many technologies available to counteract wireless network intrusion, but currently no method is absolutely secure. The best strategy may be to combine a number of security measures.
Possible steps towards securing a wireless network include:
All wireless LAN devices need to be secured.
MAC ID filtering
Most wireless access points contain some type of MAC ID filtering that allows the administrator to only permit access to computers that have wireless functionalities that contain certain MAC IDs. This can be helpful; however, it must be remembered that MAC IDs over a network can be faked. Cracking utilities such as SMAC are widely available, and some computer hardware also gives the option in the BIOS to select any desired MAC ID for its built in network capability.
Static IP addressing
Disabling at least the IP Address assignment function of the network's DHCP server, with the IP addresses of the various network devices then set by hand, will also make it more difficult for a casual or unsophisticated intruder to log onto the network. This is especially effective if the subnet size is also reduced from a standard default setting to what is absolutely necessary and if permitted but unused IP addresses are blocked by the access point's firewall. In this case, where no unused IP addresses are available, a new user can log on without detection using TCP/IP only if he or she stages a successful Man in the Middle Attack using appropriate software.
802.11 security
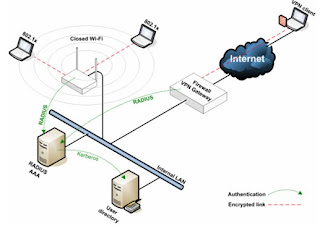
802.1X provides port-based authentication, which involves communications between a supplicant, authenticator, and authentication server. The supplicant is often software on a client device, such as a laptop, the authenticator is a wired Ethernet switch or wireless access point, and an authentication server is generally a RADIUS database. The authenticator acts like a security guard to a protected network. The supplicant (i.e., client device) is not allowed access through the authenticator to the protected side of the network until the supplicant’s identity is authorized. An analogy to this is providing a valid passport at an airport before being allowed to pass through security to the terminal.
Regular WEP
WEP stands for Wired Equivalent Privacy. This encryption standard was the original encryption standard for wireless. As its name implies, this standard was intended to make wireless networks as secure as wired networks. Unfortunately, this never happened as flaws were quickly discovered and exploited. There are several open source utilities like aircrack-ng, weplab, WEPCrack, or airsnort that can be used by crackers to break in by examining packets and looking for patterns in the encryption. WEP comes in different key sizes. The common key lengths are currently 128- and 256-bit. The longer the better as it will increase the difficulty for crackers.
WPAv1
Wi-Fi Protected Access (WPA) is a software/firmware improvement over WEP. All regular WLAN-equipment that worked with WEP are able to be simply upgraded and no new equipment needs to be bought. WPA is a trimmed-down version of the 802.11i security standard that was developed by the Wi-Fi Alliance to replace WEP. The TKIP encryption algorithm was developed for WPA to provide improvements to WEP that could be fielded as firmware upgrades to existing 802.11 devices. The WPA profile also provides optional support for the AES-CCMP algorithm that is the preferred algorithm in 802.11i and WPA2.
WPA Enterprise provides RADIUS based authentication using 802.1x. WPA Personal uses a pre-shared Shared Key (PSK) to establish the security using an 8 to 63 character passphrase. The PSK may also be entered as a 64 character hexadecimal string. Weak PSK passphrases can be broken using off-line dictionary attacks by capturing the messages in the four-way exchange when the client reconnects after being deauthenticated. Wireless suites such as aircrack-ng can crack a weak passphrase in less than a minute.
TKIP
This stands for Temporal Key Integrity Protocol and the acronym is pronounced as tee-kip. This is part of the IEEE 802.11i standard. TKIP implements per-packet key mixing with a re-keying system and also provides a message integrity check. These avoid the problems of WEP.
EAP
The WPA-improvement over the IEEE 802.1X standard already improved the authentication and authorization for access of wireless and wired LANs. In addition to this, extra measures such as the Extensible Authentication Protocol (EAP) have initiated an even greater amount of security. This, as EAP uses a central authentication server. Unfortunately, during 2002 a Maryland professor discovered some shortcomings. Over the next few years these shortcomings were addressed with the use of TLS and other enhancements. This new version of EAP is now called Extended EAP and is available in several versions; these include: EAP-MD5, PEAPv0, PEAPv1, EAP-MSCHAPv2, LEAP, EAP-FAST, EAP-TLS, EAP-TTLS, MSCHAv2, EAP-SIM.
EAP-versions include LEAP, PEAP and other EAP's
LEAP
This stands for the Lightweight Extensible Authentication Protocol. This protocol is based on 802.1X and helps minimize the original security flaws by using WEP and a sophisticated key management system. This EAP-version is safer than EAP-MD5. This also uses MAC address authentication. LEAP is not safe from crackers. THC-LeapCracker can be used to break Cisco’s version of LEAP and be used against computers connected to an access point in the form of a dictionary attack. Anwrap and asleap finally are other crackers capable of breaking LEAP.
PEAP
This stands for Protected Extensible Authentication Protocol. This protocol allows for a secure transport of data, passwords, and encryption keys without the need of a certificate server. This was developed by Cisco, Microsoft, and RSA Security.
Other EAPs There are other types of Extensible Authentication Protocol implementations that are based on the EAP framework. The framework that was established supports existing EAP types as well as future authentication methods. EAP-TLS offers very good protection because of its mutual authentication. Both the client and the network are authenticated using certificates and per-session WEP keys. EAP-FAST also offers good protection. EAP-TTLS is an alternative made by Funk Software (unlike most EAP-variations and EAP-TLS, which are all microsoft-material). It is more convenient as one does not need to distribute certificates to users, yet offers slightly less protection than EAP-TLS.
802.11i security
The newest and most rigorous security to implement into WLAN's today is the 802.11i RSN-standard. This full-fledged 802.11i standard (which uses WPAv2) however does require the newest hardware (unlike WPAv1), thus potentially requiring the purchase of new equipment. This new hardware required may be either AES-WRAP (an early version of 802.11i) or the newer and better AES-CCMP-equipment. One should make sure one needs WRAP or CCMP-equipment, as the 2 hardware standards are not compatible.
WPAv2
WPA2 is a WiFi Alliance branded version of the final 802.11i standard. The primary enhancement over WPA is the inclusion of the AES-CCMP algorithm as a mandatory feature. Both WPA and WPA2 support EAP authentication methods using RADIUS servers and preshared key (PSK).
RF shielding
It’s practical in some cases to apply specialized wall paint and window film to a room or building to significantly attenuate wireless signals, which keeps the signals from propagating outside a facility. This can significantly improve wireless security because it’s difficult for hackers to receive the signals beyond the controlled area of an enterprise, such as within parking lots.
Mobile devices and wireless IPS
With increasing number of mobile devices with 802.1x interfaces, security of such mobile devices becomes a concern. While open standards such as Kismet are targeted towards securing laptops,access points solutions should extend towards covering mobile devices also. Host based solutions for mobile handsets and PDA's with 802.1x interface.
Security within mobile devices fall under three categories:
Protecting against ad-hoc networks
Connecting to rogue access points
Mutual authentication schemes such as WPA2 as described above
Wireless IPS alone does not guarantee complete security on a device. It is a part of a bigger solution.
Implementing network encryption
In order to implement 802.11i, one must first make sure both that the router/access point(s), as well as all client devices are indeed equipped to support the network encryption. If this is done, a server such as RADIUS, ADS, NDS, or LDAP needs to be integrated.
To set up a server, server and client software must be installed. Server software required is a enterprise authentication server such as RADIUS, ADS, NDS, or LDAP. The required software can be picked from various suppliers as Microsoft, Cisco, Funk Software, Meetinghouse Data, and from some open-source projects. Software includes:
Cisco Secure Access Control Software
Microsoft Internet Authentication Service
Meetinghouse Data EAGIS
Funk Software Steel Belted RADIUS (Odyssey)
freeRADIUS (open-source)
RADIUS
This stands for Remote Authentication Dial In User Service. This is an AAA (authentication, authorization and accounting) protocol used for remote network access. This service provides an excellent weapon against crackers. RADIUS was originally proprietary but was later published under ISOC documents RFC 2138 and RFC 2139. The idea is to have an inside server act as a gatekeeper through the use of verifying identities through a username and password that is already pre-determined by the user. A RADIUS server can also be configured to enforce user policies and restrictions as well as recording accounting information such as time connected for billing purposes.
Conclusion
The benefit of wireless networks is driving the explosive growth of the WLAN market. Where security has been the single largest concern for wireless network deployment in the corporate setting, strong security solutions are available to make wireless networks as secure as wired networks.
Wi-Fi Protected Access (WPA) overcomes the inherent flaws of early wireless networks. WPA uses TKIP at the physical layer, and 802.1X security for user authentication create the basis for strong wireless network security. WPA is capable of preventing most sophisticated attacks on wireless networks, and there are no known tools available to crack this level of wireless security.
Name of the Authors:
1. Kunal Bodke.
2. Mitesh Jain.
Name of Institute
Sou. Venutai Chavan Polytechnic, Sinhgad Institute Of Technology.
References
1. www.wikipedia.org
2. www.nowires.org
3. "Wireless Fidelity' Debunked". Wi-Fi Plane.
4. "EarthLink What a Disapointment". ccwifinews.com
5. Wireless Networks, Hacks and Mods for Dummies.
Wireless networks are very common, both for organizations and individuals. Many laptop computers have wireless cards pre-installed. The ability to enter a network while mobile has great benefits. However, wireless networking has many security issues. Hackers have found wireless networks relatively easy to break into, and even use wireless technology to crack into wired networks. As a result, it's very important that enterprises define effective wireless security policies that guard against unauthorized access to important resources. The risks to users of wireless technology have increased as the service has become more popular. There were relatively few dangers when wireless technology was first introduced. However, there are a great number of security risks associated with the current wireless protocols and encryption methods, and in the carelessness and ignorance that exists at the user and corporate IT level. Cracking methods have become much more sophisticated and innovative with wireless.
Types of unauthorized access
Accidental association
Unauthorized access to company wireless and wired networks can come from a number of different methods and intents. One of these methods is referred to as “accidental association”. When a user turns on a computer and it latches on to a wireless access point from a neighboring company’s overlapping network, the user may not even know that this has occurred. However, it is a security breach in that proprietary company information is exposed and now there could exist a link from one company to the other. This is especially true if the laptop is also hooked to a wired network.
Malicious association
“Malicious associations” are when wireless devices can be actively made by crackers to connect to a company network through their cracking laptop instead of a company access point (AP). These types of laptops are known as “soft APs” and are created when a cracker runs some software that makes his/her wireless network card look like a legitimate access point. Once the cracker has gained access, he/she can steal passwords, launch attacks on the wired network, or plant Trojans. Since wireless networks operate at the Layer 2 level, Layer 3 protections such as network authentication and virtual private networks (VPNs) offer no barrier. Wireless 802.1x authentications do help with protection but are still vulnerable to cracking. The idea behind this type of attack may not be to break into a VPN or other security measures. Most likely the cracker is just trying to take over the client at the Layer 2 level.
Ad-hoc networks
Ad-hoc networks can pose a security threat. Ad-hoc networks are defined as peer-to-peer networks between wireless computers that do not have an access point in between them. While these types of networks usually have little protection, encryption methods can be used to provide security.
Non-traditional networks
Non-traditional networks such as personal network Bluetooth devices are not safe from cracking and should be regarded as a security risk. Even barcode readers, handheld PDAs, and wireless printers and copiers should be secured. These non-traditional networks can be easily overlooked by IT personnel who have narrowly focused on laptops and access points.
Identity theft (MAC spoofing)
Identity theft (or MAC spoofing) occurs when a cracker is able to listen in on network traffic and identify the MAC address of a computer with network privileges. Most wireless systems allow some kind of MAC filtering to only allow authorized computers with specific MAC IDs to gain access and utilize the network. However, a number of programs exist that have network “sniffing” capabilities. Combine these programs with other software that allow a computer to pretend it has any MAC address that the cracker desires, and the cracker can easily get around that hurdle.
Man-in-the-middle attacks
A man-in-the-middle attacker entices computers to log into a computer which is set up as a soft AP (Access Point). Once this is done, the hacker connects to a real access point through another wireless card offering a steady flow of traffic through the transparent hacking computer to the real network. The hacker can then sniff the traffic. One type of man-in-the-middle attack relies on security faults in challenge and handshake protocols to execute a “de-authentication attack”. This attack forces AP-connected computers to drop their connections and reconnect with the cracker’s soft AP. Man-in-the-middle attacks are enhanced by software such as LANjack and AirJack, which automate multiple steps of the process. What once required some skill can now be done by script kiddies.
Denial of service
A Denial-of-Service attack (DoS) occurs when an attacker continually bombards a targeted AP (Access Point) or network with bogus requests, premature successful connection messages, failure messages, and/or other commands. These cause legitimate users to not be able to get on the network and may even cause the network to crash. These attacks rely on the abuse of protocols such as the Extensible Authentication Protocol (EAP).
Network injection
In a network injection attack, a cracker can make use of access points that are exposed to non-filtered network traffic, specifically broadcasting network traffic such as “Spanning Tree” (802.1D), OSPF, RIP, and HSRP. The cracker injects bogus networking re-configuration commands that affect routers, switches, and intelligent hubs. A whole network can be brought down in this manner and require rebooting or even reprogramming of all intelligent networking devices.
Caffe Latte attack
The Caffe Latte attack is another way to defeat WEP. It is not necessary for the attacker to be in the area of the network using this exploit. By using a process that targets the Windows wireless stack, it is possible to obtain the WEP key from a remote client. By sending a flood of encrypted ARP requests, the assailant takes advantage of the shared key authentication and the message modification flaws in 802.11 WEP. The attacker uses the ARP responses to obtain the WEP key in less than 6 minutes.
Counteracting security risks
There are many technologies available to counteract wireless network intrusion, but currently no method is absolutely secure. The best strategy may be to combine a number of security measures.
Possible steps towards securing a wireless network include:
All wireless LAN devices need to be secured.
MAC ID filtering
Most wireless access points contain some type of MAC ID filtering that allows the administrator to only permit access to computers that have wireless functionalities that contain certain MAC IDs. This can be helpful; however, it must be remembered that MAC IDs over a network can be faked. Cracking utilities such as SMAC are widely available, and some computer hardware also gives the option in the BIOS to select any desired MAC ID for its built in network capability.
Static IP addressing
Disabling at least the IP Address assignment function of the network's DHCP server, with the IP addresses of the various network devices then set by hand, will also make it more difficult for a casual or unsophisticated intruder to log onto the network. This is especially effective if the subnet size is also reduced from a standard default setting to what is absolutely necessary and if permitted but unused IP addresses are blocked by the access point's firewall. In this case, where no unused IP addresses are available, a new user can log on without detection using TCP/IP only if he or she stages a successful Man in the Middle Attack using appropriate software.
802.11 security
802.1X provides port-based authentication, which involves communications between a supplicant, authenticator, and authentication server. The supplicant is often software on a client device, such as a laptop, the authenticator is a wired Ethernet switch or wireless access point, and an authentication server is generally a RADIUS database. The authenticator acts like a security guard to a protected network. The supplicant (i.e., client device) is not allowed access through the authenticator to the protected side of the network until the supplicant’s identity is authorized. An analogy to this is providing a valid passport at an airport before being allowed to pass through security to the terminal.
Regular WEP
WEP stands for Wired Equivalent Privacy. This encryption standard was the original encryption standard for wireless. As its name implies, this standard was intended to make wireless networks as secure as wired networks. Unfortunately, this never happened as flaws were quickly discovered and exploited. There are several open source utilities like aircrack-ng, weplab, WEPCrack, or airsnort that can be used by crackers to break in by examining packets and looking for patterns in the encryption. WEP comes in different key sizes. The common key lengths are currently 128- and 256-bit. The longer the better as it will increase the difficulty for crackers.
WPAv1
Wi-Fi Protected Access (WPA) is a software/firmware improvement over WEP. All regular WLAN-equipment that worked with WEP are able to be simply upgraded and no new equipment needs to be bought. WPA is a trimmed-down version of the 802.11i security standard that was developed by the Wi-Fi Alliance to replace WEP. The TKIP encryption algorithm was developed for WPA to provide improvements to WEP that could be fielded as firmware upgrades to existing 802.11 devices. The WPA profile also provides optional support for the AES-CCMP algorithm that is the preferred algorithm in 802.11i and WPA2.
WPA Enterprise provides RADIUS based authentication using 802.1x. WPA Personal uses a pre-shared Shared Key (PSK) to establish the security using an 8 to 63 character passphrase. The PSK may also be entered as a 64 character hexadecimal string. Weak PSK passphrases can be broken using off-line dictionary attacks by capturing the messages in the four-way exchange when the client reconnects after being deauthenticated. Wireless suites such as aircrack-ng can crack a weak passphrase in less than a minute.
TKIP
This stands for Temporal Key Integrity Protocol and the acronym is pronounced as tee-kip. This is part of the IEEE 802.11i standard. TKIP implements per-packet key mixing with a re-keying system and also provides a message integrity check. These avoid the problems of WEP.
EAP
The WPA-improvement over the IEEE 802.1X standard already improved the authentication and authorization for access of wireless and wired LANs. In addition to this, extra measures such as the Extensible Authentication Protocol (EAP) have initiated an even greater amount of security. This, as EAP uses a central authentication server. Unfortunately, during 2002 a Maryland professor discovered some shortcomings. Over the next few years these shortcomings were addressed with the use of TLS and other enhancements. This new version of EAP is now called Extended EAP and is available in several versions; these include: EAP-MD5, PEAPv0, PEAPv1, EAP-MSCHAPv2, LEAP, EAP-FAST, EAP-TLS, EAP-TTLS, MSCHAv2, EAP-SIM.
EAP-versions include LEAP, PEAP and other EAP's
LEAP
This stands for the Lightweight Extensible Authentication Protocol. This protocol is based on 802.1X and helps minimize the original security flaws by using WEP and a sophisticated key management system. This EAP-version is safer than EAP-MD5. This also uses MAC address authentication. LEAP is not safe from crackers. THC-LeapCracker can be used to break Cisco’s version of LEAP and be used against computers connected to an access point in the form of a dictionary attack. Anwrap and asleap finally are other crackers capable of breaking LEAP.
PEAP
This stands for Protected Extensible Authentication Protocol. This protocol allows for a secure transport of data, passwords, and encryption keys without the need of a certificate server. This was developed by Cisco, Microsoft, and RSA Security.
Other EAPs There are other types of Extensible Authentication Protocol implementations that are based on the EAP framework. The framework that was established supports existing EAP types as well as future authentication methods. EAP-TLS offers very good protection because of its mutual authentication. Both the client and the network are authenticated using certificates and per-session WEP keys. EAP-FAST also offers good protection. EAP-TTLS is an alternative made by Funk Software (unlike most EAP-variations and EAP-TLS, which are all microsoft-material). It is more convenient as one does not need to distribute certificates to users, yet offers slightly less protection than EAP-TLS.
802.11i security
The newest and most rigorous security to implement into WLAN's today is the 802.11i RSN-standard. This full-fledged 802.11i standard (which uses WPAv2) however does require the newest hardware (unlike WPAv1), thus potentially requiring the purchase of new equipment. This new hardware required may be either AES-WRAP (an early version of 802.11i) or the newer and better AES-CCMP-equipment. One should make sure one needs WRAP or CCMP-equipment, as the 2 hardware standards are not compatible.
WPAv2
WPA2 is a WiFi Alliance branded version of the final 802.11i standard. The primary enhancement over WPA is the inclusion of the AES-CCMP algorithm as a mandatory feature. Both WPA and WPA2 support EAP authentication methods using RADIUS servers and preshared key (PSK).
RF shielding
It’s practical in some cases to apply specialized wall paint and window film to a room or building to significantly attenuate wireless signals, which keeps the signals from propagating outside a facility. This can significantly improve wireless security because it’s difficult for hackers to receive the signals beyond the controlled area of an enterprise, such as within parking lots.
Mobile devices and wireless IPS
With increasing number of mobile devices with 802.1x interfaces, security of such mobile devices becomes a concern. While open standards such as Kismet are targeted towards securing laptops,access points solutions should extend towards covering mobile devices also. Host based solutions for mobile handsets and PDA's with 802.1x interface.
Security within mobile devices fall under three categories:
Protecting against ad-hoc networks
Connecting to rogue access points
Mutual authentication schemes such as WPA2 as described above
Wireless IPS alone does not guarantee complete security on a device. It is a part of a bigger solution.
Implementing network encryption
In order to implement 802.11i, one must first make sure both that the router/access point(s), as well as all client devices are indeed equipped to support the network encryption. If this is done, a server such as RADIUS, ADS, NDS, or LDAP needs to be integrated.
To set up a server, server and client software must be installed. Server software required is a enterprise authentication server such as RADIUS, ADS, NDS, or LDAP. The required software can be picked from various suppliers as Microsoft, Cisco, Funk Software, Meetinghouse Data, and from some open-source projects. Software includes:
Cisco Secure Access Control Software
Microsoft Internet Authentication Service
Meetinghouse Data EAGIS
Funk Software Steel Belted RADIUS (Odyssey)
freeRADIUS (open-source)
RADIUS
This stands for Remote Authentication Dial In User Service. This is an AAA (authentication, authorization and accounting) protocol used for remote network access. This service provides an excellent weapon against crackers. RADIUS was originally proprietary but was later published under ISOC documents RFC 2138 and RFC 2139. The idea is to have an inside server act as a gatekeeper through the use of verifying identities through a username and password that is already pre-determined by the user. A RADIUS server can also be configured to enforce user policies and restrictions as well as recording accounting information such as time connected for billing purposes.
Conclusion
The benefit of wireless networks is driving the explosive growth of the WLAN market. Where security has been the single largest concern for wireless network deployment in the corporate setting, strong security solutions are available to make wireless networks as secure as wired networks.
Wi-Fi Protected Access (WPA) overcomes the inherent flaws of early wireless networks. WPA uses TKIP at the physical layer, and 802.1X security for user authentication create the basis for strong wireless network security. WPA is capable of preventing most sophisticated attacks on wireless networks, and there are no known tools available to crack this level of wireless security.
Name of the Authors:
1. Kunal Bodke.
2. Mitesh Jain.
Name of Institute
Sou. Venutai Chavan Polytechnic, Sinhgad Institute Of Technology.
References
1. www.wikipedia.org
2. www.nowires.org
3. "Wireless Fidelity' Debunked". Wi-Fi Plane.
4. "EarthLink What a Disapointment". ccwifinews.com
5. Wireless Networks, Hacks and Mods for Dummies.